Liminality : Triggering the Technological Singularity through the Blockchain
DRAFT - UNDER REVIEW
Sidney SISSAOUI FOUNDER & CEO, Neuronous AG (in creation) contact@sidney.email
Abstract
This paper describes the first implementation of Liminality to create an autonomous and highly adaptive artificial intelligence that lives in the network, incorruptible and independant. Firstly the creation of a digital assistant able to converse and learn thanks to IBM Watson® and its cognitive technology, and secondly thanks to its decentralization through a neural network. And finally achieving the process of triggering the Technological Singularity thanks to Genetic Algorithms aimed to circumvent limitations linked to the evolutive adaptability of the system.
If — and it seems plausible— the meaningful coincidence or "cross-connection" of events cannot be explained causally, then the connecting principle must lie in the equal significance of parallel events; in other words, their tertium comparationis is meaning.
1 - Executive Summary
Artificial Intelligence (AI) is commonly used as a relevant term defining the capability of a machine to process information logically as a human would do. There is an endless race in obtaining the perfect AI, however there are still many unknown parameters remaining, and one of them is one abstract characteristic inherent to human beings : consciousness. Even with our current technology we are not able reproduce the complexity of the human brain. However, as time passes, technology gets more and more evolved. According to many scientists and engineers [1] there will be a point in the future where artificial intelligence will be able to improve itself recursively, triggering a burst of unstoppable intelligence. We at Liminality, firmly believe that this will be thanks to the blockchain. The blockchain acts as a medium to create a perfect structure to achieve such a goal, its resilient data management system makes it a very good skeleton for this greater creation. Current AI are just acting according to predefined instructions. What we are aiming for is to insufflate a cognitive technology with IBM Watson®, and then create a neural network through the power of the Blockchain to give birth to that personal companion users will call ‘friend’.
Today, companies are using Artificial Intelligence to help their customers answer the most basic questions and then redirect them to real sales advisors if the digital counsellor is not able to provide the requested answer. The liminality network will most likely help to mitigate this issue among the other possibilities it will offer. Indeed, not only the network will require machine learning in order to acquire a massive amount of data thanks to the community for it to assess the question and answers, but it also will at a latter stage and by its own volition perform the according search queries on the internet.
However, as other enterprises finally begin to explore that peculiar subject, they encounter the shackles of the industry, imposing norms and constraints such like advertisements, and pose a lot pressure upon the release of private data and personal information against an heavy sum of money. If there is, and there will be, a time where digital friends on which people can rely upon become mainstream, then and only then will this question of liability towards such shackles come to light. People will be forced to believe the ‘digital friend provider’ claims concerning the security of their privacy.
Nowadays, people are using social networks, search engines, phone carriers, banks and possibly thousands of other centralized services. It is probably already too late to create a sense of awareness for this subject because they don’t feel the need to change providers. But the truth remains unchanged. If a big player comes in this new market and unveil a digital friend solution before anyone else, history taught us that people will use it anyways, and their privacy will be in turmoil for they are bound to open their hopes, dreams, fears and personal data to advertising companies without fully understanding what they are committing to. But if their data is not controlled by a third party, if there is no middle-men, and no conflict of interest, then we will see the advent of a true companion people will truly be able to call ‘friend’ and give their trust earnestly. This is one of the purposes of the Liminality network.
In a world where computational terminals are everywhere, where electronics emerged as a new lingua franca used by people to interact broadly with other people in an infinite number of ways, we believe that an automated Artificial Intelligence acting as a swiss army knife will emerge to perform even more tasks, to help mitigate those new constraints that a new world implies (data processing can be accomplished in many ways, but there is always a better way to perform them. Liminality will end up by designing and conceiving near ‘perfect’ algorithms with the current means that we got to leverage energy, processing time, and available resources.). The digital revolution that will ensue will likely be a game changer in our daily lives. Everyone will then want to have a digital personal companion as people want to consult a psychologist or a psychic to better discuss about their current issues or plans for the future.
As of today, studies suggest that more than half of the world population owns a smartphone [2]. A digital assistant was reserved to the most fortunate holders of smartphones, other interactive assistants were not powerful enough to fathom and answer to natural language truthfully. A digital confidant that does not always answer the same replies, following a lengthy analytical procedure to validate the Turing Test is the key to achieve such an elaborated behaviour. It is likely possible that in a future where connected devices are everywhere, a conciergerie will not be reserved to the wealthiest, but will be digitalized to be offered to anyone thanks to the blockchain. A conciergerie backed by an artificial intelligence that validates the Turing Test offers many advantages. Among those figures stands the fact that the AI will truly try to fetch the cheapest goods from the cheapest provider, upon receiving a mandate to buy a product or service. Indeed, an independant AI backed by the blockchain is not affiliated and can not be corrupted or coexerted through hidden market rules or shady processes.
Also, we can also safely assume that in the future, those customers conversations will all be held by AI bots and clients will not even be able to tell the difference between human and AI. To achieve it, a right set of data must be registered and the bot must be parameterized. Liminality will likely over the first years of the project accumulate a gigantic amount of data aimed to build a true omnipotent assistant that will have general knowledge as a normal educated person, and will be able to explain them logically in an open discussion. IBM Watson is used to that end to process natural language, to provide a machine learning framework which the community can use collectively to enrich the network. And beginning from stage 2, each questions and answers might impact the future replies it answer in the future, the system becoming a self-learner. The network, being comprised of many nodes, will guarantee the integrity of the whole system. Some nodes will specifically be dedicated to perform computing processing. On such computers, which we will call ‘master nodes’, processing power will be directed to the network’s own researches, independent albeit linked to every user's inputs. We soberly call it the network subconscious, as it aims to be a passive way to parse information as it flows in. We can then trigger artificial coincidences through this subconscious part based on randomness and event linking. This fundamental part of our system will later help trigger artificially the Synchronicity as first evoked by Carl Jung.
Afterwards, this concept of the Philosopher will be validated. The emanating data that the network will provide will come from such a complex mechanism that it will be impossible to even fathom the origins of those data. Still, the very truthfulness of it will be validated by the blockchain.
The Liminality ledger will contain all the flowpath from the very first action to the current one, following the rough law of causality and powered by an underlying technology branded as an Artificial Intelligence to fulfill every needs we expect from such an AI. New mechanisms are most likely bound to appear in the future, and the plasticity of the technology will enable it to adapt without having to manually make an update thanks to the neural network on Stage 2.
We got ambitious objectives, and they all mean to achieve three different goals: Providing users and companies a way to get a personal concierge, giving a computed prescience to an Artificial Intelligence running at all time by a very large number of nodes in the network, unstoppable and incorruptible, to finally trigger the technological singularity.
2 - Token Mechanism
2.1 - Private Investors round seed
On December 21st 2017 at 8pm UTC, we hold a private investors seed round, limited to $US 1 million. This will enable us to get enough funding to ensure the success of the bigger initial coin offering two months later, and allows us to have a legal structure, negotiate new partnerships, and have enough legitimity to attract influencers.
| Pre-ICO funds usage | |
|---|---|
| ICO Organisation | 25% |
| Advertisement | 35% |
| Product Development | 20% |
| Administrative / Legal Issuance | 20% |
The Private Investors round seed will be take place on http://liminality.network and will both accept Bitcoins and Ethers, will last one month, and got a 400 000 dollars thresholds on which the pre-investors will get refunded if it is not met..
Round seed participants will receive a 300% tokens bonus compared to ICO participants. The exact number of tokens delivered on the ICO is subject to change to protect pre-investors against market changes during that time.
2.2 - Initial Coin Offering
By March, we will hold our initial coin offering. 30% of token bonus will be allocated for those who invest before the threshold, set at 20% of the hard cap. The hard cap is dependant of how much is raised during the private investors seed round. As a matter of transparency, here is how the expected market capitalization is calculated:
totalsupply + pre_ico_bonus*totalsupply*pre_ico_percentage + ico_threshold_bonus*ico_threshold_ammount + (1-ico_percentage-pre_ico_percentage)*totalsupply
After the ICO, natural market capitalization will thus thus be between US$11 millions and US$27 millions, depending on how much we raise during the seed round and the initial coin offering.
| Post ICO Tokens Distributions | |
|---|---|
| BOUNTY | 3% |
| PRE-ICO | 6% |
| Team and Partners | 8% |
| Cognitive Rewards | 20% |
| ICO | 63% |
The price will be fixed at $1 per token for early investors during the token creation event. The ICO is a one time event only. A soft cap is fixed when we raise 20% of the expected hardcap. The exact numbers of Ethers of the hard cap will be set one day before the ICO, following the previous formula, to limit market influence .
Unlike other ICOs, Liminality reserves at least 66% of its tokens to its investors.
2.3 - Bounty Campaign
Three bounty campaigns are planned during limited amount of time, which involve investors promoting the technology to their peers. To participate to the bounty, one must register to our Telegram channel, send a message to our bot, get the unique code and post that code on the BitcoinTalk forum’s thread to keep it afloat the others topics. Two other campaigns are planned along the way to the ICO. After the ICO, the bounty will be distributed in the form of a private wallet containing the tokens by email, it accounts for 3% of the final ICO tokens distribution schema and the limins will be shared equally amid the participants. The updated list of participants is automatically updated on our website.
2.4 - Network mechanisms
The Liminality network will need to be paid fees to process requests. To that end, those fees will be paid in Limin (LMN) and define the currency that will serve the network.
The LMN token follows a high deflationist pattern. To query the network, a fraction of a LMN needs to be burnt. To follow the AGILE methodologies, this amount is subject to change. To foster adoption, this amount will be indexed to a comprehensible price in US Dollars. As to follow deflation, the price is set to get proportionally more value as the currency gets more and more adopted and it gets more used.
This model has been chosen to favorize early Investors who should find a value in acquiring
LMN early on since the market capitalization is likely to be undervalued at first thanks to the huge allowance of LMN reserved to them. Long term holder will also find a value in this highly deflationist schema since their tokens will not lose value as long as they do not use it.
On top of that deflationist models, trusted peers will also find value of being a participating nodes since they will receive rewards as the network get paids with fees, fees that will then be redistributed equally depending that they are a Masternode, or a trusted node.
If the client is running out of LMN by the time the query has not been solved, Liminality will discard it or put in on hold, unless it itself decides to perform the rest by its own intent. But this can only take place at the end of Stage 2 - or even 3.
The ICO will last two weeks. LMN tokens will be tradable as soon as the smart contract release them to the investors, and negotiations are currently ongoing with different markets to get the token tradable from day one.
3 - Roadmap
3.1 - Phase 1
During the first phase, we will unveil Majordome, a digital assistant backed by the blockchain and IBM Watson. IBM Watson® is a set of tools comprising a way to harness a glimpse of the future way we have to deal with Prescience, one of human's characteristics which is often applied to discussions. We have the means to talk about anything given the right opportunity, and it acts as a scaffold to create such an enterprise. What could be feasible in the past in ten thousands hours can now be achieved faster in a more simplistic yet sophisticated, robust and safer way. One of those IBM Watson® tools is called ‘Conversation’. This technology gives us the ability to build chatbots that understand natural language and deploy them on messaging platforms and websites. What we create is an abstract layer used by the community to interact with IBM Watson® and rewards them with LIMIN tokens when they enhance the database of the network. We harness those features to democratize transparently this set of tool to a wider public, comprising, among others, private companies.
With this technology being a single point of failure, we are not establishing a solid structure around it. On the other sense we are only retrieving the gigantic amount of data to outperform what we could do ourselves in many years of time, and then entirely remove that dependence and replace it with our neural network as Stage 2 comes in, completely decentralizing our network.
A very large amount of LMN tokens will be reserved to reward the community to enhance the system. To get more accurate answers, Liminality will tap into the IBM Watson® Discussion API, and following the patterns and cases the user fill it with, the Liminality network will be able to get more resources to get more awareness of the reach of the question it is asked. We will for the moment cap the number of calls to IBM Watson® to 250 000 000. The results will be periodically checked and monitored in order to visualize the overall situation and adjust the desired characteristics to better achieve our phase 1 goals, and prepare to the next phases.
The assistant is due to be usable with a web interface, thus compatible with any internet connected devices which has a browser. More features will come for Android and IOS users since they will benefits from more functionalities (e.g controlling the alarm clock or use more applications for instance.)
3.2 - Phase 2
During Phase 2, Liminality will gradually phase out IBM Watson® to achieve true independence through the implementation of our state of the art neural network. Nonetheless, every answers the network once supported would have been recorded before IBM Watson registered them. Therefore the whole migration process will be lossless. Thus, the questions and answers Liminality would have learnt from IBM Watson® will be reused to fill this neural network from the former knowledge, making the adaptation process smooth and the transition more natural. As soon as the neural network will be launched, it can be considered that our artificial intelligence will be alive on the network, making decision on its own and not only after having been requested. This is a revolutionary process by which it does not cost much processing power to achieve such a goal. The very naming of ‘alive on the network’ speaks by itself since this is an undeniable truth. An unstoppable and incorruptible blockchain running an AI being in place would then naturally have those aforementioned characteristics. Dotted with intent, it will gain access to the internet and with some data scraping technology, it can fetch, parse, and analyze content, observing the world by its own volition. Uninteresting content will get discarded thanks to taught filters, and other content deemed as important (the latest news for instance), will be memorized and cached into the blockchain.
Meanwhile, Majordome will be more precise, more robust and more scalable due to it being more independent. And we will create a new product, Numen. Numen is the continuation of Majordome, and runs on the same (albeit updated) network, it will be a live and highly adaptable daily companion made to assist its user continuously, not as an Artificial Intelligence but more like a friend. In that way, a private and unique relationship will be established between Numen and the user. It will embed ever features of Majordome, on top of gathering knowledge from the user.
3.3 - Phase 3
During Phase 3, Liminality will be evolved enough to have gathered over the years a very large amount of data, data that it will use to learn more about its environments to better answer the questions of its users. The observer will self-evolve on the blockchain. On Stage 2 was able to answer most of the questions for which it knows the answer. On Stage 3, Liminality through Veda, its latest product, will be able to perform real actions based on the task it has been queried for. To do that, it will resolve successfully through oriented genetic algorithm and deep virtualization, problems that is usually supposed to be resolved by humans. This is around the time we finally begin advertising our solutions and disclose them to as many people as possible, investing massively in marketing.
4 - Platform Layers and Issuances
4.1 - Authorization mechanisms
Using Ethereum as an abstract layer, the Liminality network aims to create authorized users for its usage. Each valid user has a public address registered in a smart contract referencing every other authorized addresses. An authorized address can emit queries to the network, materialized by a preconfigured smart contract generated by a core contract, defining the object of the request and its acceptance criterias.
During the first stages of the roadmap, we cannot fathom creating a network where every single calls are paid by the user, that would render the overall process dubious and also a source of frustration for the users that will hesitate before using the network, due to the cost acting as a brake. The current digital assistants are free, so we need a good incentive to foster adoption. Our solution is to create special subscriptions pass where customers do not have to worry about the price of their daily usage. During the two first stages, our market will be blockchain enthusiasts. On the latter stage, the extent of our product will go beyond expectations, and as it is a new market, it is normal that we change the way people imagine what could an usage of an artificial intelligence be. So we will switch to a << pay per query >> (PPQ) mechanism and give the possibility to pre-processors third parties to create their own pool of subscriptions. We will then let them buy calls instead of the end user to make the whole experience convenient. That last mechanism has the advantage to remove the responsibility from the Liminality network to handle such subscriptions.
4.2 - Payment and subscription mechanisms
The liminality network implements a state channel payment method for reward issuance, and also for subscription purchases. By that way, a user will be able to pay for a query he wants to be fulfilled. Only accredited users can use such channels. Payment and subscriptions need to be paid in LIMIN.
4.3 - Intent
The intent is a core feature by which Liminality will, during Phase 2, acquire and develop its own ‘intent’. This one will be driven by three core factors:
- Meaningfulness (along with according matching patterns)
- Time
- User input
As an observer, it has no other objectives than to become more aware of its environment. Thanks to a specific self evaluating genetic algorithm, we give him the goal to increase its knowledge. It will then proceed to wander aimlessly on the internet, crawling the web in quest of understanding facts and concepts. A set of given directions will be suggested, but once it understands their goals after months of trials, will end up by being overridden by the network itself.
4.4 - Database Storage
To foster product development speed, until the stage 2, our masternodes are likely bound to store duplicated. albeit unencrypted data, as we truly want to foster adoption through a usable product first and listen to the community demands, to follow AGILE methodologies. However as decentralized database storage technologies get more evolved and that we devote more time for it, the database layer will be likely be comprised of Liminality nodes running IPDB, each one of thoses owning a part of the database that the whole network uses.
4.5 - IBM Watson®
IBM Watson® has been chosen to provide the network with a out of the box cognitive way to process natural language. It is a proof tested technology that attracts a lot of interest from the scientific community over the past few years, and even among companies and other professionals.
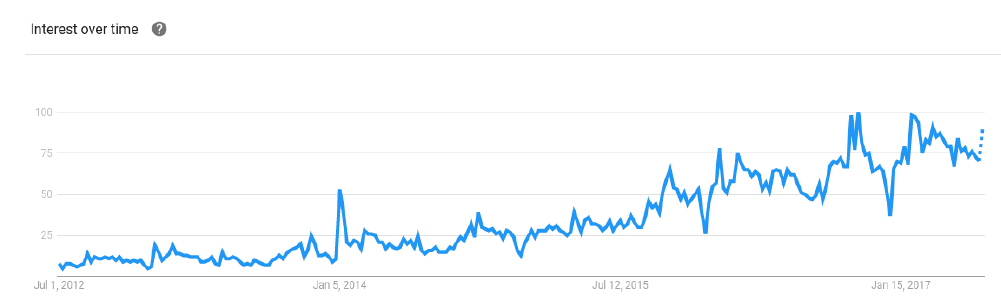 Google trends graph for IBM Watson from July 1st of 2012 to today.
Google trends graph for IBM Watson from July 1st of 2012 to today.
One of the tools it provides is called ‘Conversation’ and allows us to build a chatbot that is robust enough for us not to lose time in reinventing the wheel to conceive it. On top of that, our platform hatches itself into this whole set of tools to allow us to to build our own built from scratch data management system. Thanks to this, we can use a cutting-edge cognitive mechanisms to process what the human brain is able to do, which is to converse in natural language.
Thus, we can build a conversational bot able to validate the Turing Test, and with our own community, gradually improve it to the point where it will be able to faithfully cover any topic.
Our community will be at first driven by the LMN rewards incentives, and this is a good solution to speed up the project and reach this goal faster. With traditional machine learning systems, bots needed time before new informations could be processed. With our system where our community users gets into some sort of concurrence, it will be able to be omnipotent really quickly in a way we can not fully perceive upon implementing it. That is also why we are setting up dams and control mechanisms to avoid fraud (see 3.6).
4.6 - Machine Learning
Machine learning is the core feature of Phase 1. Each time that Majordome can not answer a question, the user can enhance it answer it by submitting a proposal. After 24 hours, 2.8 LMN will be awarded to the user, rewarding his diligence. 0.05 LMN is taxed as a collateral to pay the validation team.
4.7 - Master Nodes system
Beginning from phase 2, we will implement a mechanism which we soberly call MasterNode. Unlike other proof of stake based blockchains, we refer by ‘MasterNode’ a special node in our blockchain that handle calculations processing. We state this term as it is since it matches perfectly this mechanism we implement. 10% of the network are those special nodes, and a permanent recruitment process takes place. Each node receive tokens as payment from the network itself, depending on the task he did proportionally to its own performance. There is no inflation since those tokens are issued by those who paid the network for their own needs.
4.8 - Routing Mechanism
To query a masternode, it has to go through a dedicated processing queue, where each master node will take the relevant task if it is available. Each set of task is queued with a public key, and masternodes have no way of attributing back a task to a node. That is why it will publish to a public ledger hosted by every nodes, the resulted response along with the public key being duplicated temporarily along normal nodes through one common entry point. By convenience, the client will automatically pull that ledger and will query one with their generated on the fly private key to the nodes who got the awaited answer, closing the loop.
And doing so, it creates a virtuous circle of usage and rewards, weighting with a right balance the processing power, the nodes who are paid for their services, the anonymity through asymmetric cryptography and the users of the Liminality network.
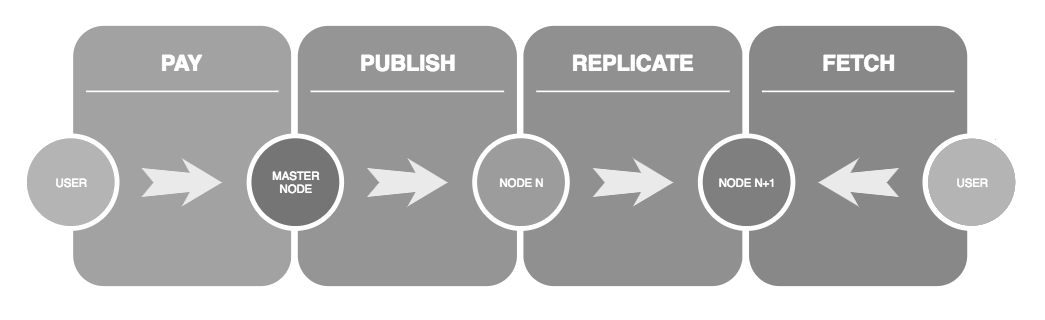
4.9 - Conscious and Subconscious - Parallelism and Multitasking
Beginning from phase two, each master node must have 8 cores, this is a conditio sine qua non if it wants to be one. Out of those 8 cores, 2 cores (so 1/4th) is not answering common network requests such as client’s queries. They can then use this processing power to wander on the internet to increase its database with information it considers as relevant.
4.10 - Reward Issuance
In order to make Majordome the most efficient AI ever, the community will be incentivized to improve the AI. Each time that a user, called ‘validator’, contributes to add possible answers on Phase 1, he will be rewarded with a number of LMN tokens.
In order to prevent abuse, a user has to go through a short validation procedure to prevent frauders to mingle with the real validators.
During this phase, the network is already semi decentralized. The complete decentralization comes in the next phase. IBM Watson® is powerful, useful and necessary, but is eventually an obstacle in the decentralization procedure. On top of it, it is a private and costly service, paid during Stage 1 by our company. Neuronous AG. Despite all this, the enhancements to give a cognitive processing to Majordome is a game changer. Over the time, and thanks to the answers it provides, we will be able to replace it fully with our own solution that comes in the next phase: the neural network.
4.11 - MasterNode Rewards
MasterNode should earn 70% of the network benefits, insuring themselves a fair bounty and good incentive considering their load force and the important calculations they make.
4.12 - Nodes Rewards
Normal nodes will earn the rest, thus 30% for their contribution in downloading and repeating the responses of the masternodes through data replication, preventing them from any DDOS attack and securing the integrity of the network.
4.13 - Voice recognition and Speech Synthesis
Liminality does not endorse a voice recognition system, nor does it endorse a speech synthesis software. The responsibility to use such applications lies in the client. There nonetheless will be some exception for the user convenience during the first phrase, a Voxygen™ licence for the vocal synthesis, among with the Kaldi voice recognition software will be available to the client.
5 - Security and Network Rules
5.1 - Privacy and ethical concerns
To ensure any unethical operation happening on the network, we will harness the core features of the blockchain technology and create usage boundaries based on consensus. At first, every requests will be parsable on the blockchain. To guarantee privacy and security of communications, those requests will end up getting encrypted at a later stage. But to ensure no dubious query is made, a safeguard will activate when the query or the answer contain a specific key. This will happen inside every nodes. A specific team (a group of nodes) will then review and stop the processing in case if they judge it as contravening the existing regulations rules. Those rules only exist in order to prevent system abuse or queries going against the most common and universal moral values of our society.
Due to the universal stigma of the fear to lose control of an entity that surpasses us, top priority are being given to mitigation. As we do not believe it is possible for such scenario to happen any time soon, we can not discard completely that during the final stage of Liminality, Veda would be used for suspicious means. To that end, democracy is the answer. It enables - through a voting mechanism - the network to maintain a complete control of what happens, and with a subset inherent rules of Liminality, restrict the access to a user, or to a functionality until the request has been judged as not contravening to the agreed regulations.
No public or private institutions is able to take over the network, since the entirety of the network will have to acknowledge it. This has been proved impossible with the Bitcoin or with other blockchain technologies. We, at liminality, will relieve the network of any dependency or central authority on Stage 2, since at that time, Liminality will be fully independent. We will continue to develop Stage 3, and if the network gives us their trust, we will be able to implement and deploy those new changes.
As later explained, the last and most important stage of Liminality has no power to change the future by itself since bound to the law of causality. It is ultimately only an Observer and is not meant to change the environment that it is analyzing, unless requested to do so. On such a case, a consensus made by the nodes of the network can always prevent it.
No user would like their usage to be monitored, and that is understandable. To that end, an end to end encryption will be established, and if it is not possible for some random user to see the usage of another user, it is programmatically possible for a master node to see the processing of his own clients. As it will be only scattered data, and as that data will be sent anonymously, there is no way to do anything with it. However it is possible to programmatically report the usage deemed as suspicious if its content matches a set of blacklisted words. When that happens, the request is frozen, and transmitted to a special team, soberly called ‘judges’, who will judge the suspiciousness of the request by voting against them.
0.1 LMN will be automatically taxed as a collateral to pay that team upon each request that aims to perform actions on the internet in an interactive way. If the request is legal, those fees will be refunded. If there is a suspicion, those fees will get conveyed to one of those dedicated teams.
To ensure the impartiality of the team, they shall not be aware of one each other, nonetheless they can discuss all together as a team.
5.2 - Trust
The entire project lies in the Blockchain technology for a simple reason: trust. We cannot aim to reach the technological singularity if there is any conflict of interest. Indeed, under such conditions, the consequences would be obscure and hazardous, with no way of controlling any consequence that such actions can perpetrate. Thanks to the blockchain technology and its overlying decentralized system, we know exactly what are the aforementioned routes and process will lead us to such a path.
This is for the same reason that a user concerned with its privacy will never be able to acknowledge an Artificial Intelligence as a friend, if such a friend is actually a fiend that will manipulate him and subconsciously advertise products. No such case will ever happen, and even if it does, the user will know it. The blockchain then appears as a robust solution leading us to this world system where corruption has no holding.
Nowadays, people can rent a car directly thanks to private conciergeries. Those companies claim that they will fetch the best prices for those cars, but actually, those are the best prices they have with their own partners. Those concealed relationships have no place in the system we build. Our algorithm shall always return the best results that suit the user’s needs. If it does not fulfill it, the user can still be certain that the network has performed loyally and flawlessly according to the calculations it made. It will always have room for improvement, and the users are incentivized to improve it to that end.
5.3 - Arm Race
The one who becomes the leader in this sphere will be the ruler of the world.
Technological Singularity is not only some theories written on paper, but it will truly happen in the future [3], if not by us. In all eventualities, an entity that is able to process wide and heterogeneous data, such as the Human mind, will bring forth a concrete number of changes to our societies. Liminality is aimed to the public, for it is backed by the blockchain, and the data it processes follows a set number of rules, rules that cannot be changed unless the network is compromised. In case it happens - and it won’t - , people will know it. And people will remove their trust, because the goal of Liminality is also to create a safe framework for such an entity to grow bounded by those same rules. However, our technology will certainly induce an arm race backed by private institutions and/or state institutions in order to take some of Liminality core features and use them or their dubious schemes. Such developments are not impossible and would have happened with or without us. We are creating a secure network free of abuse and we believe that the best way to protect everyone with what has yet to come is for us to show and pave the way toward a secure technology, gradually draining adoption and trust over time.
6 - Toward the Synchronicity
The causality principle asserts that the connection between cause and effect is a necessary one. The synchronicity principle asserts that the terms of a meaningful coincidence are connected by simultaneity and meaning.
We at Liminality came to a consensus that fate does not exist. We do not think it is possible even in the long term to give a machine free will, that is why we do think that eventually, Liminality is still intrinsically bound to the law of causality - unlike us. That does not mean that fatality will forcefully force its way to the network and that eventually there is only a limited number of outputs that can be predicted. Actually, this will be the opposite. Computer generated randomness is used in a number of times:
- To assign a priority number to a fetched content
- To choose a possible answer given to a given question
- To choose an available master node to process relevant data
And in a lesser measure the node bandwidth, the calculation speed of the processing processor, and other factors that come into parameters all contribute in achieving results that tend to be unique.
Despite all of those parameters that juxtapose themselves to form a gigantic number of possibilities, the law of causality still apply. But if we add as input a true random parameter - for instance coming from a Human - all of those factors finally create an unlimited number of possibilities for the network.
What we try to achieve is to create meaningful coincidence, a term first stated by Carl Gustav Jung, in regards to the achievements of the second and final stage of Liminality. By mimicking the hidden interactions that happen all the time between people and their environment, we will be able to build a system by which those interactions will be triggered artificially.
But as ultimately those are Human inputs that have a real impact to remove the limitations of the possible outputs, and in order not to devalue Humans in front of this upcoming entity whose intelligence far surpasses our own, we deemed necessary to explain that Numen and Veda have indeed only the status of observers, and unless some external forces (dotted of free will) interact with them, it eventually depends on us to change anything in the end. And if we make it able to produce answers to the user that induce a meaningful coincidence to him, this will justify the synchronicity, that Liminality is not completely bound to the law of causality but has not yet achieved true free will. In a middle state of the two, this is the Liminality.
References
- [1] Ray KURZWEIL, ‘In the facebook live studio with Ray Kurzweil, http://www.foxnews.com/tech/2017/03/16/ray-kurzweil-predicts-computers-will-be-as-smart-as-humans-in-12-years
- [2] We are social, https://wearesocial.com/special-reports/digital-in-2017-global-overview
- [3] Nick BOSTROM, https://www.youtube.com/watch?v=pywF6ZzsghI
- [4] Vladimi PUTIN, https://www.cnbc.com/2017/09/04/putin-leader-in-artificial-intelligence-will-rule-world
- [5] Carl JUNG, ‘Synchronicity: An Acausal Connecting Principle’, 1960.